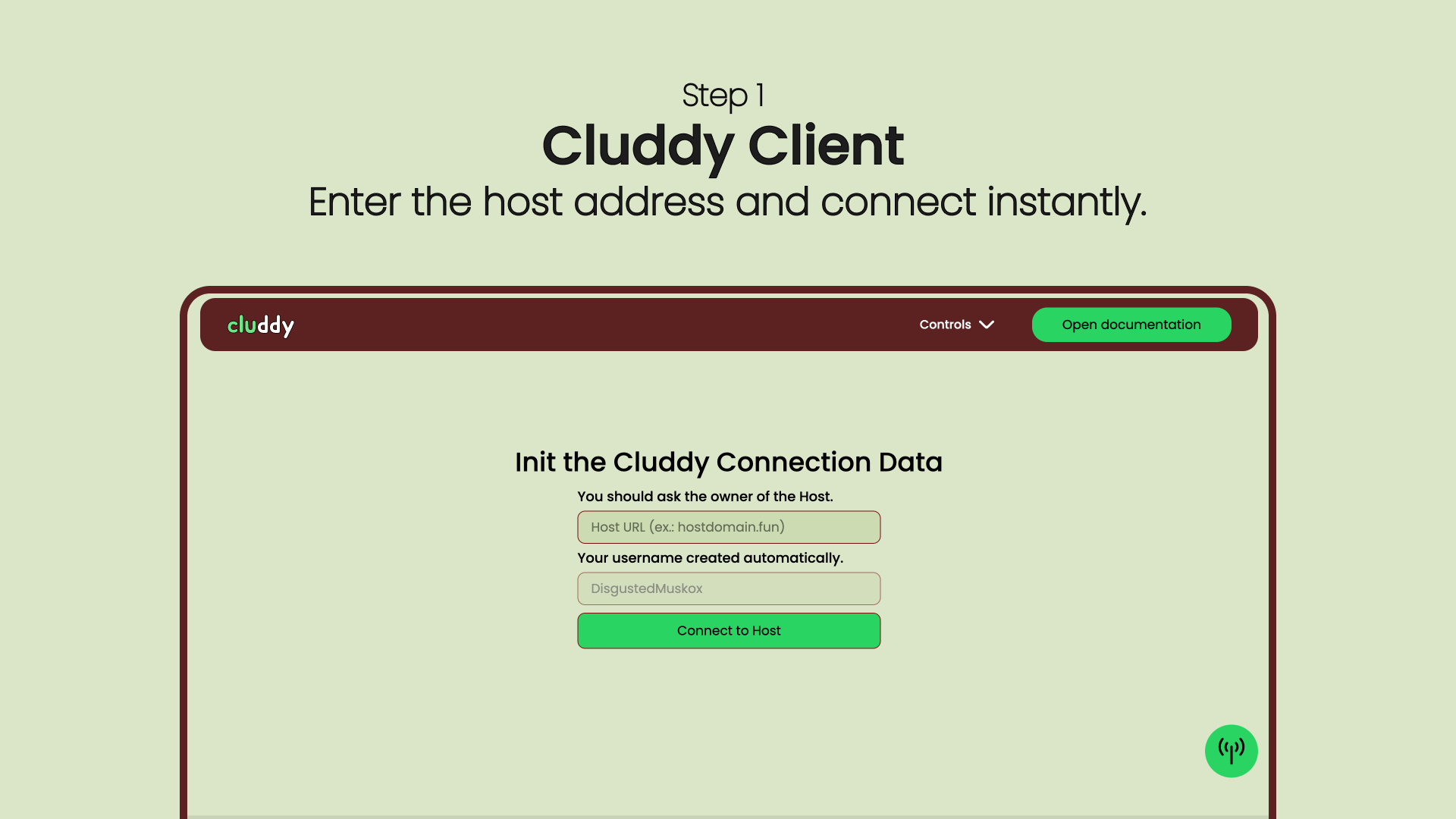
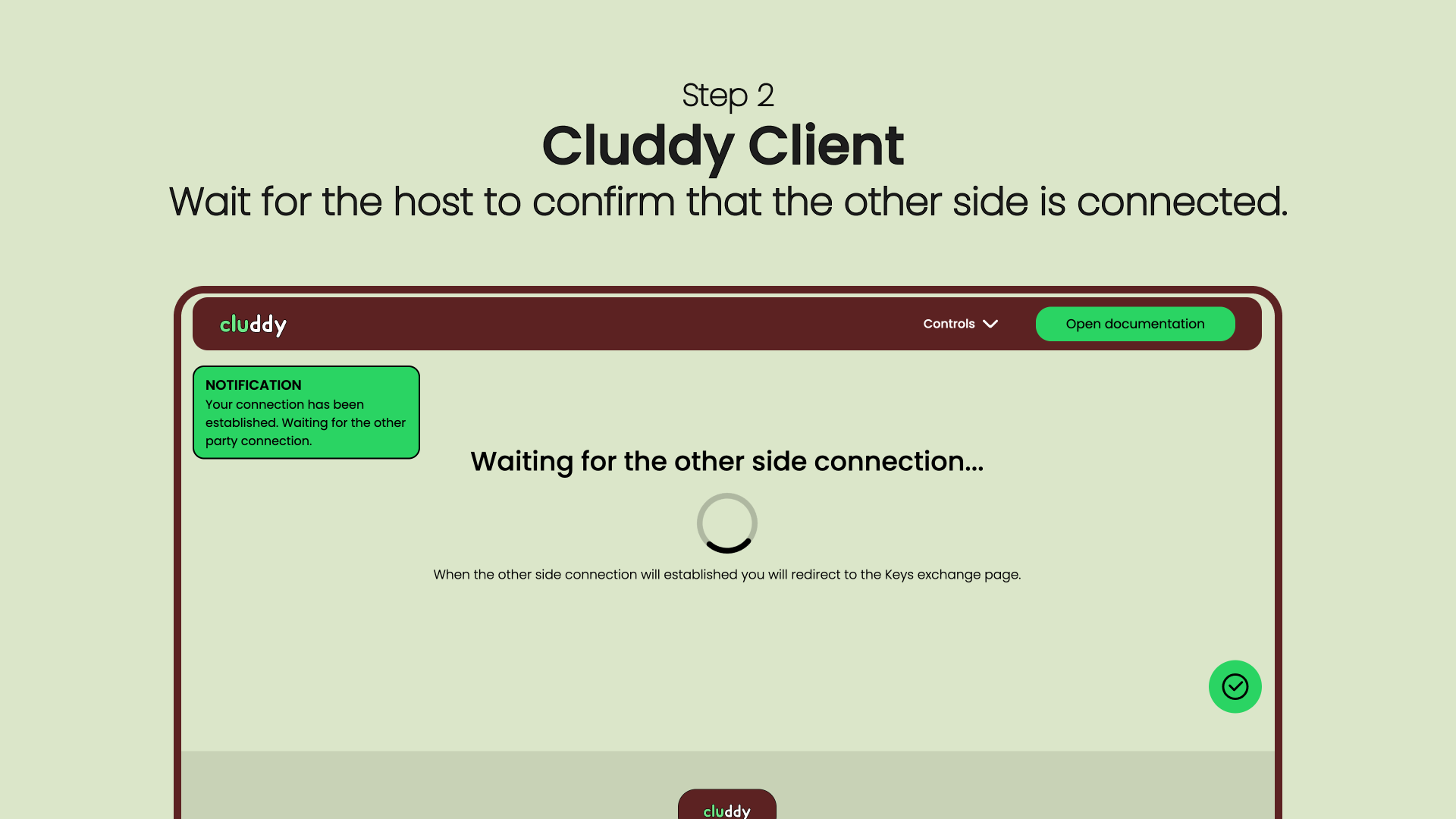
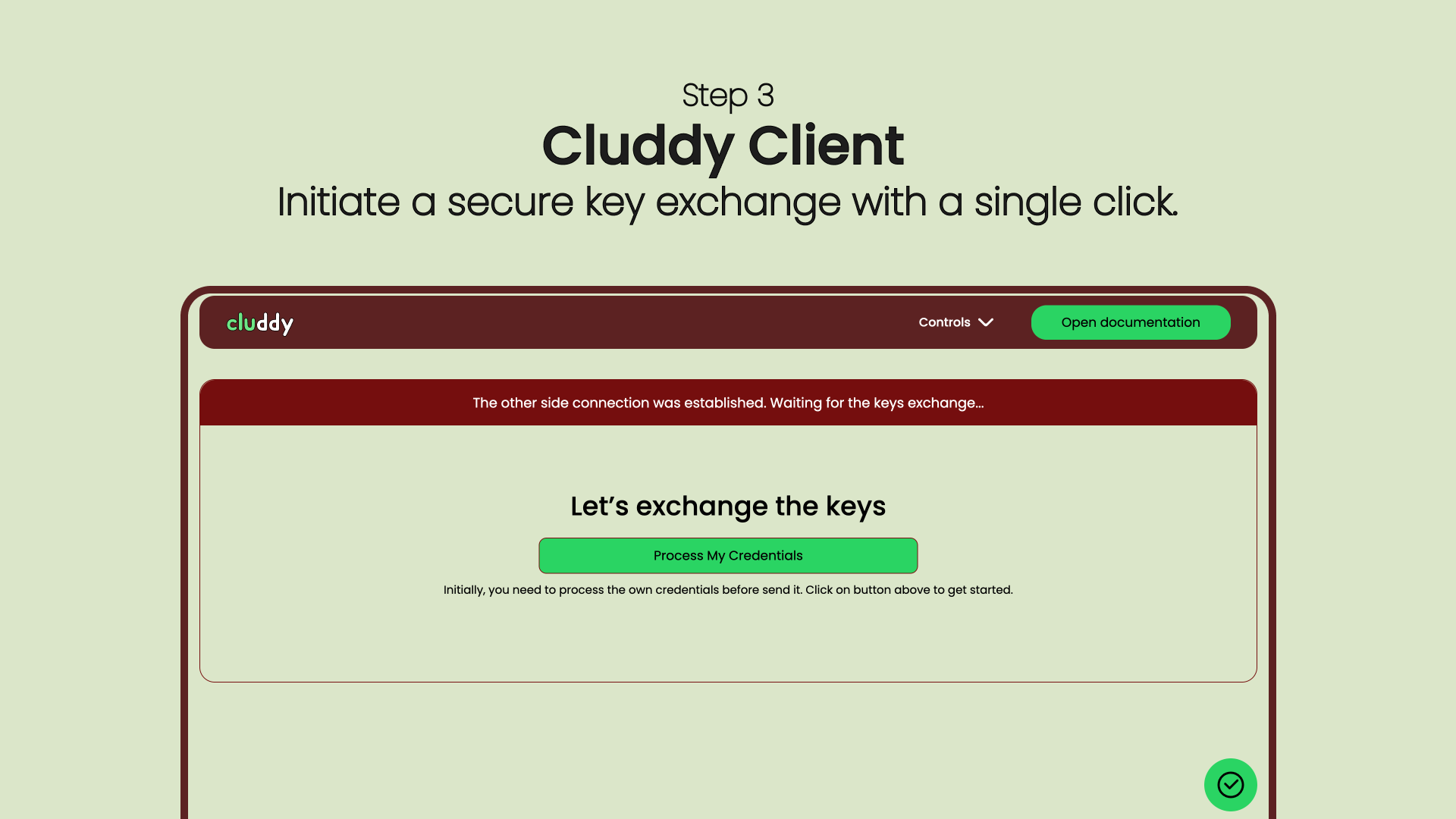
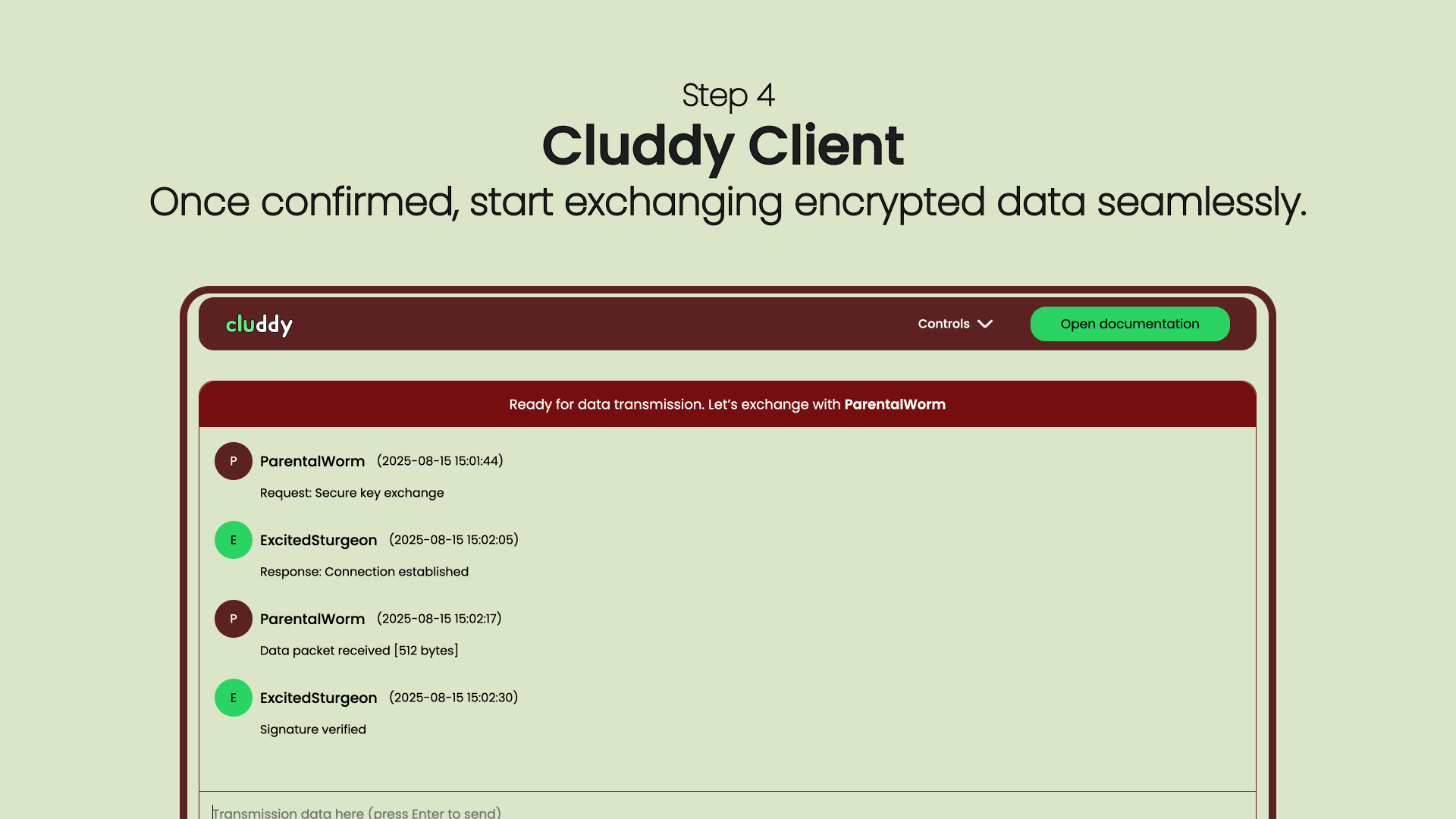
Cluddy is not a VPN. It doesn’t reroute all your traffic or hide your IP — instead, it builds a dedicated, encrypted tunnel only for the data you choose to exchange.
You run Cluddy on your own VPS and local clients, keeping full control over keys, routing, and encryption. No intermediaries. No stored data. No profiling.